Delta Executor has quickly become one of the most advanced and trusted Roblox executors available today. Designed for mobile and desktop users who want full control over their Roblox experience, Delta delivers powerful script execution, fast performance, and modern security across iOS, Android, and macOS. In this complete guide, you will learn exactly what Delta Executor is, how it works, … How to Install Delta Executor on iOS 26 and Android – A Complete GuideRead more
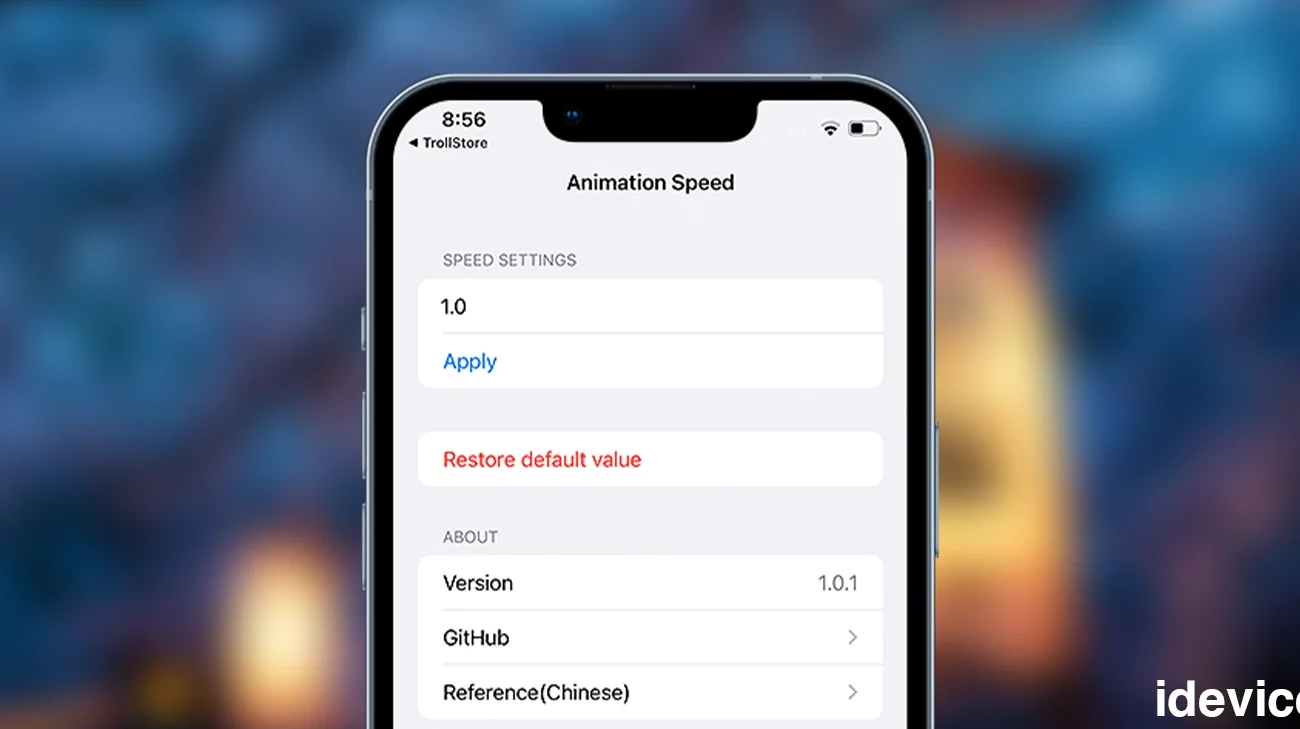
AnimationSpeed IPA – Customize UI Animation Speed on TrollStore Devices (iOS 14 – 17.0)
Apple locks iOS to a single, fixed animation speed, but with AnimationSpeed, you finally get full control. This TrollStore-exclusive utility lets you speed up or slow down UI animations across the entire system, giving your device a snappier, more responsive feel. AnimationSpeed IPA works on iOS 14 – 17.0, comes with an updated interface, English language support, and a proper … AnimationSpeed IPA – Customize UI Animation Speed on TrollStore Devices (iOS 14 – 17.0)Read more
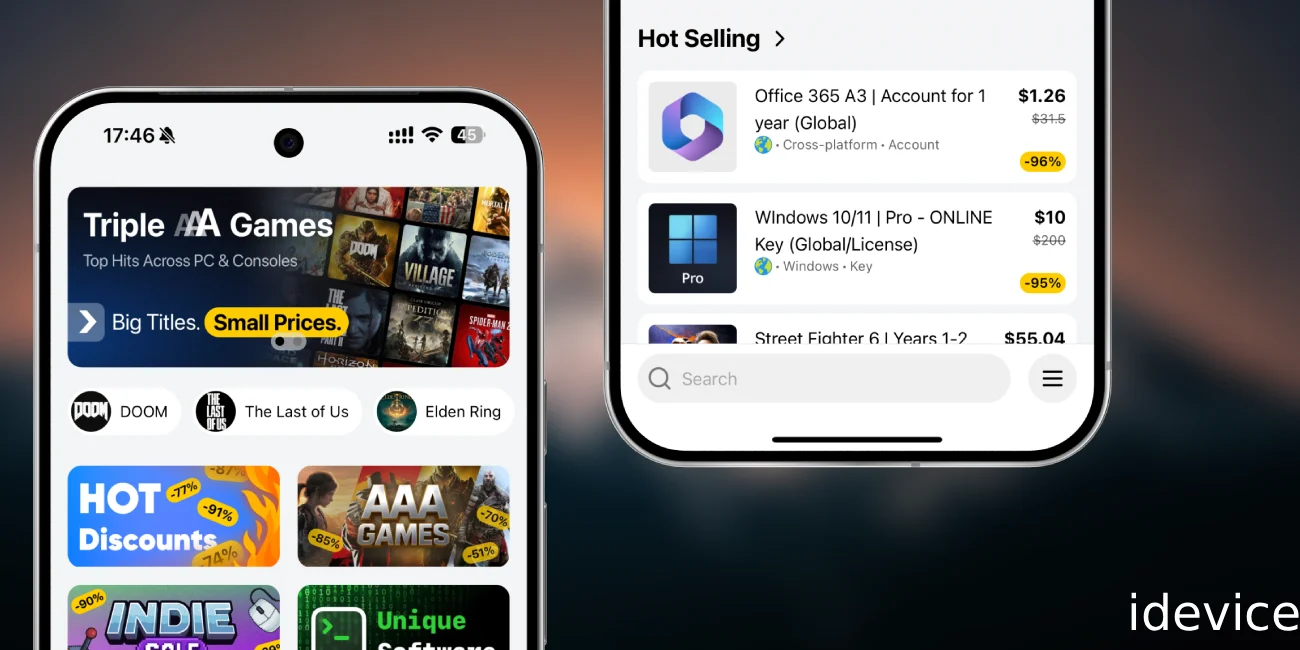
AltMarket: A Surprisingly Easy Way to Get Cheap Windows & Office Keys
Buying software keys online can feel like a gamble. A lot of discount key sites are vague about where their keys come from, they hide company information, they offer confusing or nonexistent refund policies, and support can be unreliable. Many customers end up with invalid licenses, already used codes, or keys that are tied to questionable sources. AltMarket is different. … AltMarket: A Surprisingly Easy Way to Get Cheap Windows & Office KeysRead more
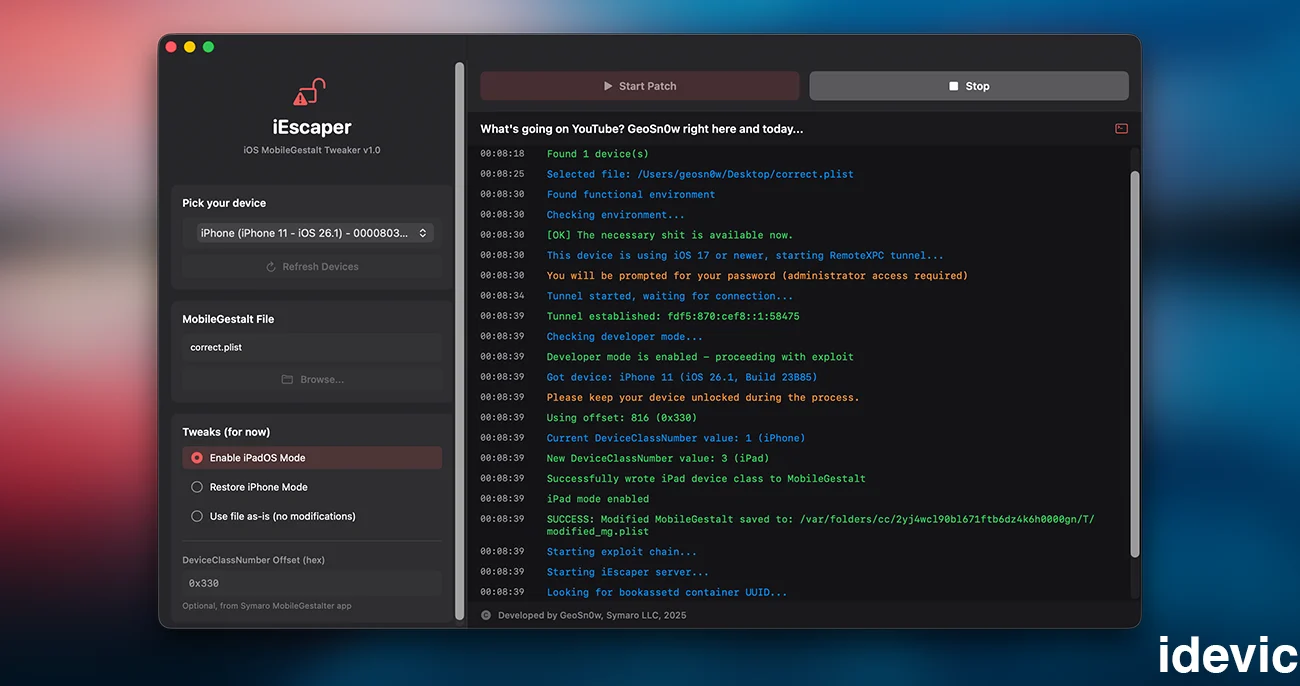
Download iEscaper – iOS MobileGestalt Tweaker for iOS 17.0 – 26.1 for All Devices
Hi everyone, GeoSn0w here! Today, I am excited to release iEscaper v1.0. I built this tool to bring powerful MobileGestalt tweaks to users on newer iOS without requiring a jailbreak. iEscaper is based on the new bookrestore sandbox escape exploit, and I rewrote the entire exploit in Swift for improved reliability and stability. The result is a tool that has … Download iEscaper – iOS MobileGestalt Tweaker for iOS 17.0 – 26.1 for All DevicesRead more
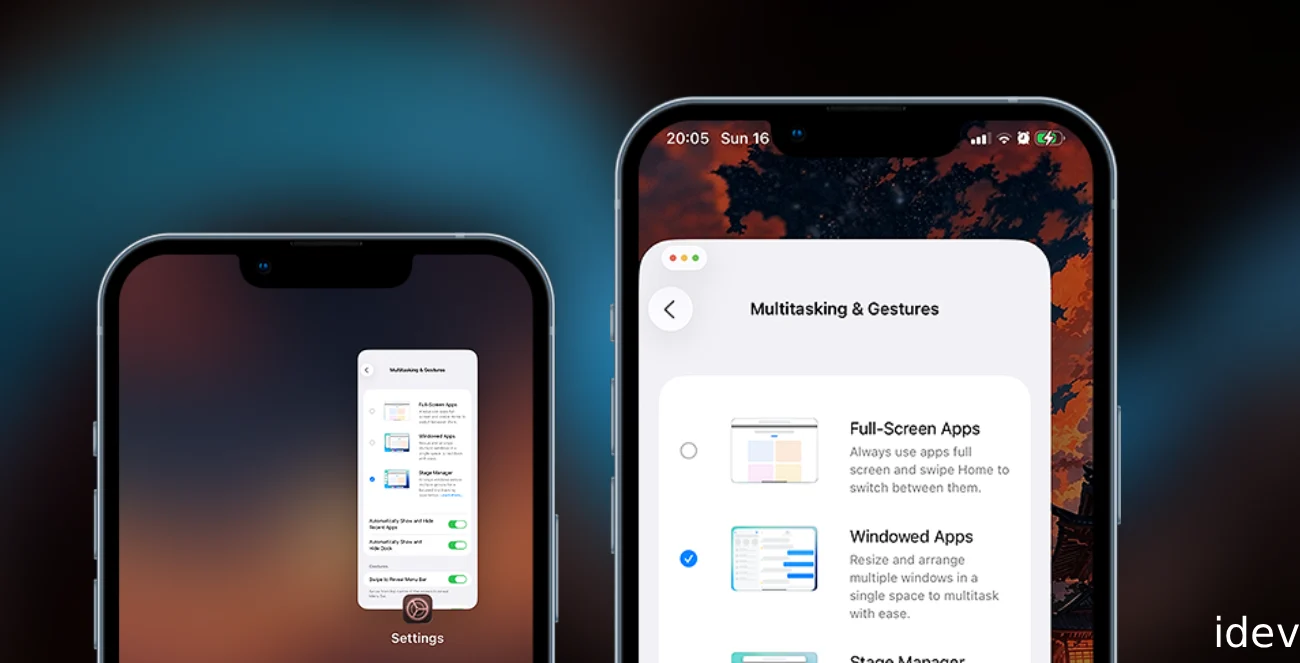
How to Enable iPad Features like MultiTasking & Stage Manager on iPhone via MobileGestalt
The newly released itunesstored & bookassetd sbx escape exploit allows us to modify the MobileGestalt.Plist file to change values inside of it. This file is very important since it contains all the details about the device. Its type, color, model, capabilities like Dynamic Island, Stage Manager, multitasking, etc. are all present inside that file. Naturally, Apple has encrypted the key-value … How to Enable iPad Features like MultiTasking & Stage Manager on iPhone via MobileGestaltRead more
Solved! How to Jailbreak iCloud Locked iPhone 2025
Jailbreaking remains a topic of steady interest among iPhone users who want deeper access to their devices. When an iPhone is locked behind Activation Lock, many users wonder if a jailbreak can help them regain access. There is a lot of confusion about what is possible, what is not, and what tools exist today. This guide covers the realities of … Solved! How to Jailbreak iCloud Locked iPhone 2025Read more
How to Transfer WhatsApp from iPhone to iPhone
Switching to a new iPhone is exciting, faster performance, better cameras, and new features. But one question always comes up: how do I transfer WhatsApp from my old iPhone to my new one? If you’re like most users, your WhatsApp messages hold years of conversations, precious photos, and important files. You don’t want to lose any of that during the … How to Transfer WhatsApp from iPhone to iPhoneRead more
iPhone Locked to Owner? Here’s How to Unlock It Safely
Buying a used iPhone can be a great way to save money until you see that dreaded message on the screen: “iPhone Locked to Owner.” At that point, your excitement quickly turns into frustration. You can’t access the phone, can’t set it up, and can’t use it unless you have the previous owner’s Apple ID and password. If this sounds … iPhone Locked to Owner? Here’s How to Unlock It SafelyRead more
Vsave for iOS: The Best Free FB Video Downloader for iPhone Users
For many iOS users, video content on social platforms has become an essential part of daily entertainment, learning, and communication. While streaming works well with a stable internet connection, there are plenty of situations where saving videos locally is more convenient. This growing demand has led to the rise of reliable video downloader apps that help users store content for … Vsave for iOS: The Best Free FB Video Downloader for iPhone UsersRead more
How to use AltMarket.app: The New Digital Storefront for Discounted Keys, Games, and Software
If you’ve been on the internet as much as I am, stores like AltMarket selling discounted software keys are nothing new for you either. There are lots of such services online, but many of them are shady as all heck. You look at their terms and conditions, and you can find no info about who is behind that company, what … How to use AltMarket.app: The New Digital Storefront for Discounted Keys, Games, and SoftwareRead more