To protect your jailbroken iOS device from malware and viruses, you first need to understand where this kind of threat comes from. In recent months the amounts of malware in the jailbreak community have grown significantly, mostly due to a pirate repo called “MainRepo” which spreads botnet malware onto the jailbroken device unfortunate enough to install pirated tweaks from there.
The malware in the jailbreak community has always been present, but with very low levels of infection and not much to worry about. However, in 2021 the “MainRepo” malware showed the jailbreaks a different face of the tools they use.
What is the “MainRepo” malware and how it works?
First identified by tweak developer @opa334dev, the malware was remotely installed by the pirate repo onto the user’s devices and it allowed the repo to control the device remotely by sending commands over the network. These commands would run as root thanks to crux, a small command-line utility used to run commands with root privileges. The malware would then be able to execute any commands the attacker wanted on the user’s devices at a moment’s notice, thus creating a basic botnet of jailbroken devices.
Developer @opa334dev has first called “MainRepo” off on Twitter when he found out how the malware worked.
The mainrepo malware (“MobileSafeMode.dylib”) sends your UUID to a server, the server then has the ability to send back any command that should be executed on your device. It’s essentially a backdoor that’s running inside SpringBoard and Cydia. pic.twitter.com/QcY4rFnRDg
— opa334 (@opa334dev) March 23, 2021
By opa334dev’s account, the malware impersonates real jailbreak components like the MobileSubstrate or MobileSafeMode and other such files, in order to avoid being deleted by the user. What is worse, even if the user deletes the pirated tweak, the malware persists on their device.
The control is done through the Unique Device Identification Number which they collect when they first run the malware in the background on the device. Using this unique ID they can then send any commands they want to a particular device, or a group of devices thus creating a botnet.
A few days after opa334dev’s discovery, the well-known Antivirus company, ESET Research, has also done an analysis on the malware, pretty much confirming opa334dev’s findings and assigning a name to the malware. They called it “iOS/Spy.Postlo.A”.
#ESETresearch can confirm this great find by @opa334dev. The mentioned dylib binary is indeed malicious iOS tweak that allows the attacker to execute shell commands on a jailbroken and compromised iOS device @cherepanov74 1/5 https://t.co/bdGCX2mTBx
— ESET research (@ESETresearch) March 25, 2021
How can you protect your jailbroken device from malware?
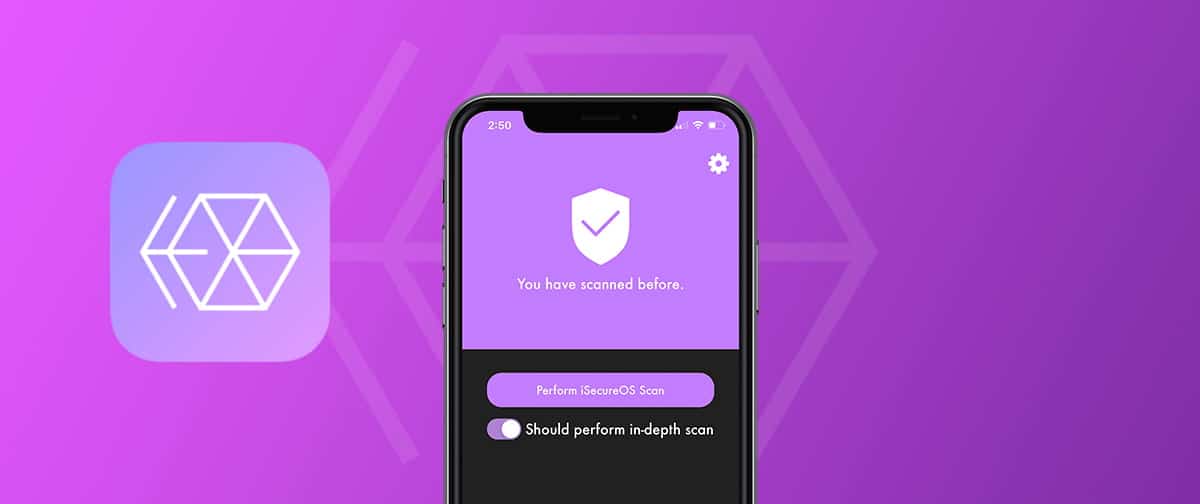
Coincidence has it that right at the time the aforementioned events were unfolding, developer GeoSn0w, was already working on a jailbreak tweak/app called iSecureOS, which is an anti-malware tool/security application for jailbroken devices.
The tweak itself is completely free and it analyzes the files on the device and looks for possible malware. The tool also gives several safety tips to the user if various settings need to be turned on for better protection, or if the device is vulnerable.
iSecureOS is compatible with all three major jailbreaks at the moment, CheckRa1n, Unc0ver, and Taurine Jailbreak. It also works on Odyssey Jailbreak, Chimera Jailbreak, and any other jailbreak for iOS 12 onwards.
iSecureOS is fully open-source, and thus, everybody can see how it works and what code it runs on the device. The source code is available on the official iSecureOS GitHub repository.
How to install iSecureOS on your jailbroken device?
Installing the iSecureOS tweak is fairly simple to do, and can be done from Cydia, Sileo, Zebra, or any other package manager. Please follow the steps below to install iSecureOS on your device:
- Add the official iSecureOS repo: //isecureos.idevicecentral.com/repo
- Inside the repo, there’s only one tweak: iSecureOS. Install the tweak the way you’d install any other tweak.
- A new application called “iSecureOS” will be available on your device after installation.
- Open the application and run a scan.
Here’s a video that demonstrates how to use iSecureOS on your jailbroken device:
What devices and iOS versions are supported by iSecureOS?
All devices running iOS 12 or newer are supported, including the A12, A13, and A14 devices with all popular jailbreaks. Also, iSecureOS can be installed from any package manager, or directly using the apt binary via command-line / SSH.
What’s the difference between a normal scan and an in-depth scan in iSecureOS?
The normal scan will take a look at the files stored in the default dylibs folder of your jailbreak, where all the tweak dylibs are placed when you install a tweak in Cydia / Sileo. These dylib files are being injected into the appropriate processes and they patch the code of normal iOS programs to change their behavior. This is how the iOS tweaks work, and it’s a prime target for malware.
The in-depth scan will scan the aforementioned folder, but it will also scan other folders and binaries which are not necessarily tweaks, such as the jailbreak bootstrap files, and other jailbreak executables that may be altered by malware.
Note: If the normal scan yields malware results, it’s a very good idea to perform an in-depth scan as well, because it means that your device is infected.
What happens when iSecureOS detects malware on my device?
If during a scan iSecureOS finds malware matching known malware in the definitions database, it will automatically be quarantined to a remote location and the file will be neutered, but not deleted. You can choose to purge the quarantine at any time in the iSecureOS settings, but once the malware is sent to the quarantine it is no longer executed by your device and cannot harm it.
We do, however, recommend purging the quarantine for good measure.
How have the attackers reacted to iSecureOS?
MainRepo, the creators of the iOS/Spy.Postlo.A malware, have indeed taken iSecureOS as a threat to their attack model, and have attempted by various means to circumvent detection either by attempting to patch iSecureOS directly or by modifying the downloaded definitions on the fly.
iSecureOS received numerous updates which killed MainRepo’s ways of defeating detection, and thanks to action taken by @opa334dev, their repo domain was taken down (mainrepo.org). Do know, however, that they’re back under a different name (mrepo.org) with the same shady practices and malware.
The newer version of iOS/Spy.Postlo.A attempts to modify the definitions of @isecureos (iOS Security application for jailbroken devices) to avoid detection. #ESETresearch 3/4 pic.twitter.com/ptcpZ6yybD
— ESET research (@ESETresearch) June 8, 2021
Is the MainRepo malware dangerous? What can it do?
Yes. The MainRepo malware is considered a spyware tool that has the potential to collect any information they want from the victim’s device, can run commands on the device, and most importantly, they can do this without leaving any trace that they did it because all the malware code runs silently in the background and the user is completely oblivious to what’s going on.
In fact, MainRepo has pushed commands to victim’s devices to prevent iSecureOS from scanning or from being installed, showing that they do pretty much weaponize their arbitrary commands execution on those devices.
If you have nothing to hide, you wouldn’t try so hard to block an anti-malware software from detecting your binaries, would you?
How can I stay secure?
To prevent malware from infecting your device, it’s best to follow the guidelines below:
- Avoid piracy. Pirate repos crack and patch tweaks to bypass DRMs and licenses, but this has the effect of no longer matching the hash of the original tweak. This way it’s impossible to tell what other nefarious modifications have been added to the tweak without having reverse engineering skills.
- If you do pirate, avoid mainrepo.org or mrepo.org. MainRepo is not a trustworthy source and they have been exposed for infecting user’s devices with spyware malware before.
- Install iSecureOS (completely free) and run scans periodically.
- Never keep the default “alpine” SSH password. iSecureOS can change the SSH password and it will prompt you to do it if it detects the default one.
- Keep your tweaks and jailbreak utility up to date.
- Do not visit shady websites on mobile. WebKit exploits can easily be deployed to exfiltrate data from your device. If in doubt, do not access the site.
With this being said, jailbreaking your iOS device is a pretty safe thing to do as long as you follow some common-sense guidelines and avoid shady repos. If you can, stick to the well-known repos like Dynastic or Chariz / Packix. Those are vetted and checked regularly. If you do decide to pirate, please use common sense and do your research.



Leave a Reply
You must be logged in to post a comment.