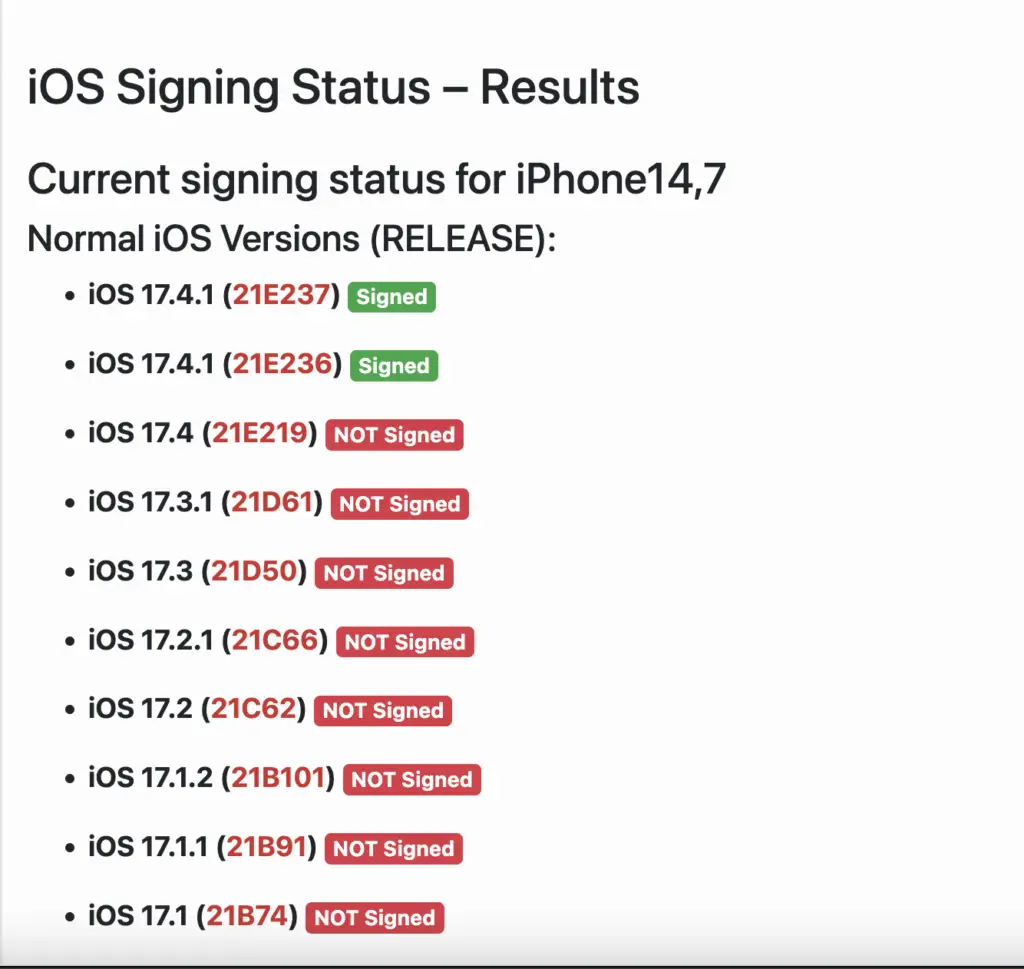
Apple finally unsigned iOS 17.3.1 for good, after re-signing it briefly once iOS 17.4 was released.
It’s unclear why Apple decided to re-sign iOS 17.3.1 after previously unsigning it, and it’s even more confusing if you consider that iOS 17.4 got unsigned with the release of iOS 17.4.1, but iOS 17.3.1 stayed signed for longer.
In any case, Apple inadvertently gave jailbreak users the chance to downgrade from iOS 17.4 and iOS 17.4.1 back to iOS 17.3.1 which is much better for jailbreak purposes for reasons we’re going to cover in this article.
Why is iOS 17.3.1 much better for jailbreaking?
Once Apple released the security content for iOS 17.4, it became clear that iOS 17.3.1 and older versions are all vulnerable to what may be a PPL or SPTM bypass, a crucial component for jailbreaking nowadays.
Apple did learn from their mistakes over time and having a kernel exploit is no longer all you need to make a jailbreak.
Nowadays even if you do manage to build a kernel exploit, memory page protections such as PPL and SPTM will prevent you from being able to run tweaks as they heavily protect the userland from any memory changes.

This does have severe implications for the jailbreak community. Not only do you need a kernel exploit but now you also need to bypass these security features which requires an additional, rarer exploit.
It is the consensus among the developers in the community that the vulnerability CVE-2024-23225 patched in iOS 17.4 is either a PPL or an SPTM bypass, hence why it is so valuable for us.
CLARIFICATION
PPL (Page Protection Layer) is available on A12+ devices.
SPTM (Secure Page Table Monitor) / TXM were introduced in A15 and iOS 17 Beta, essentially replacing PPL. SPTM works similarly to how PPL did, but it is much more robust and powerful.
So if you have an iOS 17 device, these devices into PPL devices (A12-A14) or SPTM devices (A15+), each one requires a different kind of bypass. You can find a full explanation of both on my Twitter post.
Another good-looking vulnerability patched in iOS 17.4 is CVE-2024-23288 which seems to be an AppleMobileFileIntegrity / AMFI (Code Signing) vulnerability. Could be pretty useful considering how much of a pain AMFI tends to be for jailbreaking.
What should I do if I already updated to iOS 17.4 or iOS 17.4.1?
Now that iOS 17.3.1 stopped being signed by Apple, there is not much you can do to get to a better version.
Downgrades are only possible in two scenarios:
- The iOS version you want to downgrade to is still signed by Apple.
- You have a checkm8 device (A11 and lower) and you perform a tethered downgrade.
Tools like FutureRestore + saved SHSH2 blobs don’t work anymore because of the Cryptex1 component.
Methods like DelayOTA do not work for downgrades, only for upgrades from an older iOS version.
There aren’t any methods for you to downgrade from iOS 17.4 or iOS 17.4.1 back to iOS 17.3.1 or lower at the moment.
If you are interested in jailbreaking, disable auto-updates in Settings and keep the device on the version you are on at the moment. A jailbreak will eventually come.
If you are waiting for an iOS 17.3.1 jailbreak, and you don’t have a checkm8 iPad, these vulnerabilities may help down the line so stay where you are.
More iDevice Central guides
- iOS 17 Jailbreak RELEASED! How to Jailbreak iOS 17 with PaleRa1n
- How to Jailbreak iOS 18.0 – iOS 18.2.1 / iOS 18.3 With Tweaks
- Download iRemovalRa1n Jailbreak (CheckRa1n for Windows)
- Dopamine Jailbreak (Fugu15 Max) Release Is Coming Soon for iOS 15.0 – 15.4.1 A12+
- Cowabunga Lite For iOS 16.2 – 16.4 Released in Beta! Install Tweaks and Themes Without Jailbreak
- Fugu15 Max Jailbreak: All Confirmed Working Rootless Tweaks List
- iOS 14.0 – 16.1.2 – All MacDirtyCow Tools IPAs
- iOS Jailbreak Tools for All iOS Versions
