TrollStore and subsequently TrollStore 2 are indispensable apps for jailbreak enthusiasts on iOS 14, iOS 15, 16, and even early iOS 17.
TrollStore takes advantage of a CoreTrust bug on iOS to allow apps to be sideloaded and installed permanently without having to re-sign them and without having Apple revoke them.
Aside from being able to install any IPA file, TrollStore also offers app developers and users the possibility to use any Entitlements they want, something that is normally blocked by iOS security when sideloading through normal channels (AltStore, Xcode, Sideloadly, etc.).
The entitlements can be particularly powerful, one of which allows any app to completely escape Sandbox and have access to read all files on the File System. If this sounds like a possible security issue for you, I am just getting started.
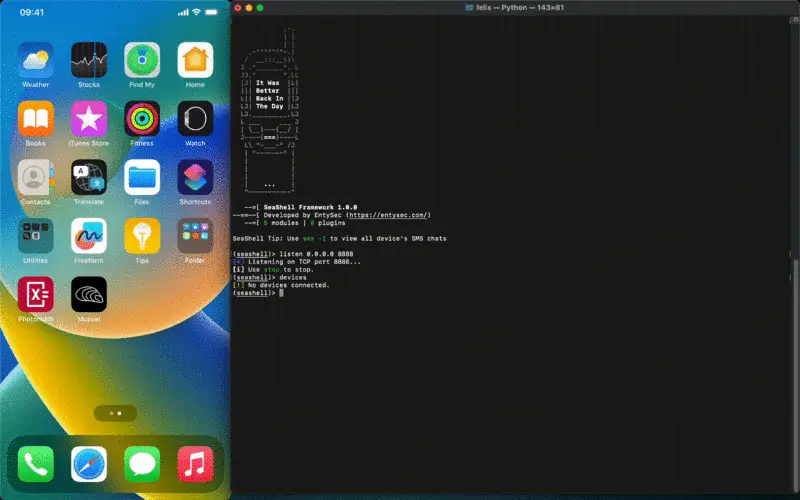
Project SeaShell, or the very first TrollStore malware
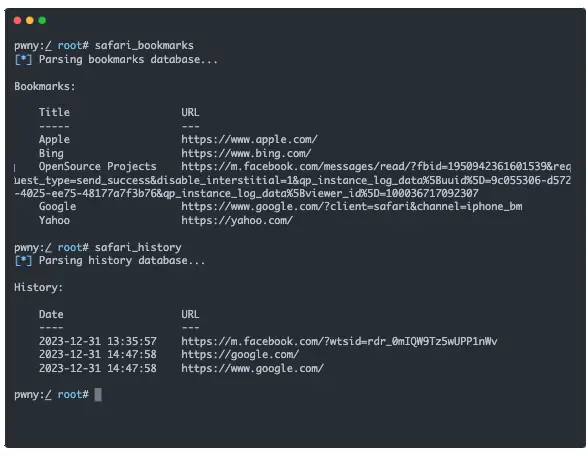
A project called SeaShell developed by EntySec as a demo attack was released today on GitHub. This is a full-blown open-source malware that abuses TrollStore to exfiltrate user data such as SMS, Photos, and Browser History, can hook/inject other apps and listen to your every move.
The project itself isn’t meant to cause harm and it is part of security research, but its components can be used by anybody to cause a lot of harm.
To make matters even scarier, the malware can be distributed as a regular IPA or its components can be bundled in another app a user may want to install.
All it takes to become infected is to install the malicious application with TrollStore and run it once. Yes, you can close it and never open it again after that, it will remain active.
Project SeaShell is more of a security research PoC than real malware, hence why it is open-source and the developers did not try to infect anybody. They merely wanted to prove a point that yes, TrollStore is very useful and powerful, but it can be weaponized against the user.
To understand how powerful SeaShell framework really is, imagine that once you run this app once, every file on your device can be transferred over the network to the attacker. Not only that, but the attacker can run any command on your device.
What iOS versions are vulnerable to this kind of attack?
If your device is compatible with TrollStore, it is vulnerable, and installing any IPA from anywhere can infect you if the source is not trusted.
We say TrollStore users are at risk, but really, this malware doesn’t need TrollStore at all. A threat actor could easily bundle up the components with the CoreTrust exploit used by TrollStore in the first place, and you wouldn’t even know.
It’s not TrollStore that causes the vulnerability, but rather the iOS version you’re on that is vulnerable to the CoreTrust bug that powers TrollStore to begin with.
iOS 14.0 up to iOS 17.0 are vulnerable on all devices.
How to protect yourself against this kind of attack?
If you are running iOS 14.0 – 17.0 you can certainly fall victim to such an attack. My biggest concern is that the components of SeaShell framework can vary easily and reliably be exploited to spy on / monitor someone’s device.
This can easily be used in an abusive relationship to keep track of the partner and everything they do on their phone.
The second this is installed on a victim’s device, everything stored on that device can be remotely accessed.
If you’re not interested in TrollStore or sideloading, updating to the latest iOS version will fix this vulnerability and render SeaShell framework and its components useless, at least for now.
If you cannot or do not want to update from your TrollStore-compatible iOS version, things get a bit complicated. I recommend the following precautions:
- Do not install any IPA or TIPA file from unknown or untrusted sources. Even developers in the community can turn rogue and inject this into a real application. I am not saying “be paranoid”, but “be cautious”.
- If you can, extract the IPA (it’s a zip archive) and check for any weird components like a mussel binary, or modified Info.plist files that may contain CFBundleBase64Hash, or anything about <host>:<port>. These can be changed by an attacker, so they are not guaranteed to be present in an attack.
- If available, compare the hash of the downloaded IPA / TIPA with the one provided by the official developer.
Realistically, there’s very little that can be done to detect or prevent a well-crafted attack based on SeaShell on TrollStore-compatible devices, so it’s best to be cautious with what IPAs or TIPAs you install, and especially from where.
Remember, SeaShell and EntySec aren’t malicious. This was released as part of their “SeaShell – iOS 16/17 Remote Access” security research, SeaShell being a demo / model attack, but the components are real and they CAN be used by a threat actor.
More iDevice Central Guides
- iOS 17 Jailbreak RELEASED! How to Jailbreak iOS 17 with PaleRa1n
- How to Jailbreak iOS 18.0 – iOS 18.2.1 / iOS 18.3 With Tweaks
- Download iRemovalRa1n Jailbreak (CheckRa1n for Windows)
- Dopamine Jailbreak (Fugu15 Max) Release Is Coming Soon for iOS 15.0 – 15.4.1 A12+
- Cowabunga Lite For iOS 16.2 – 16.4 Released in Beta! Install Tweaks and Themes Without Jailbreak
- Fugu15 Max Jailbreak: All Confirmed Working Rootless Tweaks List
- iOS 14.0 – 16.1.2 – All MacDirtyCow Tools IPAs
- iOS Jailbreak Tools for All iOS Versions
