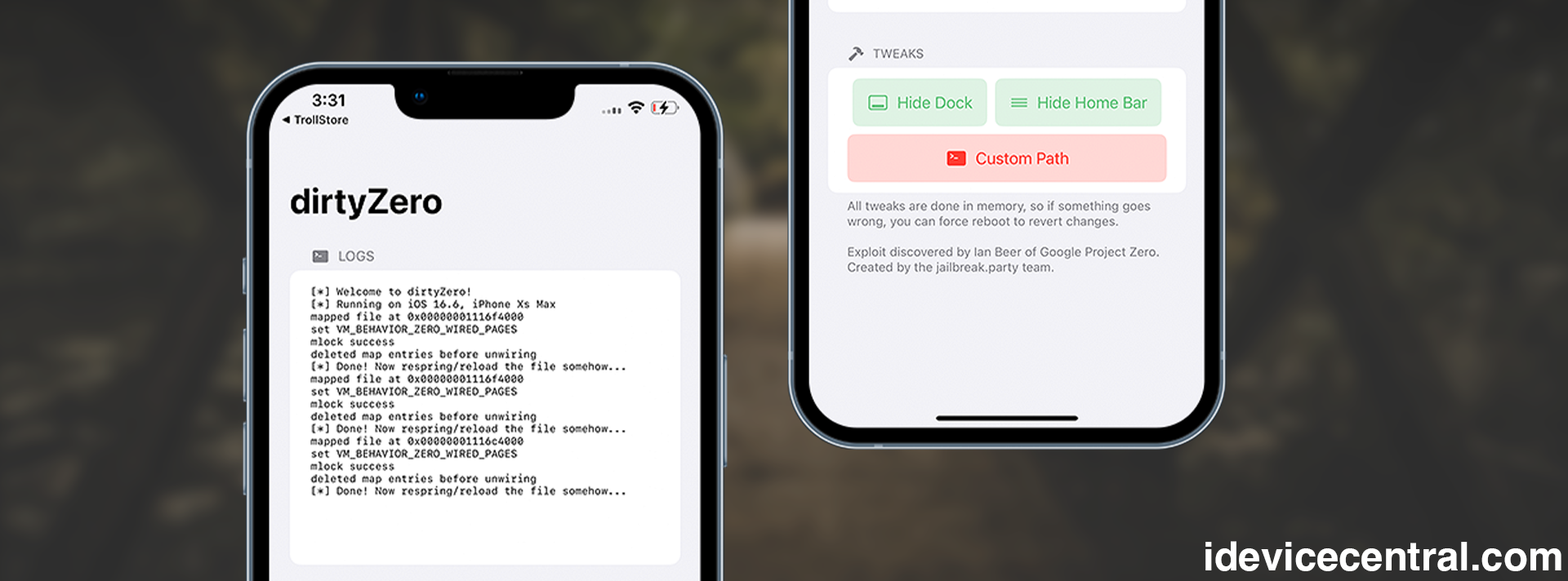
A brand new iOS customization app, dirtyZero, developed by Skadz, was released. It’s based on a newly released iOS exploit (CVE-2025-24203) by Ian Beer of Google Project Zero.
The application allows you to hide the home bar and hide the dock on iOS 16.0 all the way up to iOS 18.3.2 on all devices, providing a degree of customization akin to jailbreak tweaks without being jailbroken.
What is dirtyZero?
The dirtyZero is a free and open-source iOS customization tool that enables you to hide the home bar and the dock on iOS 16.0 – 18.3.2 without being jailbroken.
The app helps you easily customize your iOS device without having to worry about jailbreak tools, jailbreak detection, or tweaks.
iOS 18.4 is not supported because the vulnerability has presumably been patched by Apple.
Here’s the full iOS compatibility chart:
iOS Version | Support Status |
|---|---|
iOS 16.0 – iOS 16.7.10 | Supported |
iOS 17.0 – iOS 17.7.5 | Supported |
iOS 17.7.6+ | Not Supported |
iOS 18.0 – iOS 18.3.2 | Supported |
iOS 18.4+ | Not Supported |
Download dirtyZero IPA
You can download the IPA file for the dirtyZero customization app below. Since the app is completely free and open-source, you can also compile it yourself if you prefer.
You can sideload the IPA file with your favorite iOS sideloading tools such as AltStore, Sideloadly, Feather, ESign, etc.
Once installed, the application should be available on your Home Screen. Here are the currently available tweaks:
- Home Screen
- Disable Dock Background
- Disable Folder Backgrounds
- Disable Alert & Touch Backgrounds
- Disable Spotlight Backgroud
- Disable Widget Config BG
- Disable App Library BG (iOS 18 only)
- Lock Screen
- Disable Passcode Background
- Disable Lock Icon
- Disable Quick Action Icons (iOS 16 & 17 only)
- Disable Large Battery Icon (iOS 18 only)
- Global Customization
- Disable Notification Widget BGs
- Disable Home Bar
- Enable Helvetica Font
- Disable Slider Icons
- Control Center
- Disable CC Background
- Disable CC Module Background (iOS 18 only)
- Disable WiFi & Bluetooth Icons (iOS 16 & 17 only)
- Disable DND Icon
- Disable Screen Mirroring Module (iOS 16 & 17 only)
- Disable Orientation Lock Module (iOS 16 & 17 only)
- Disable Focus Module (iOS 16 & 17 only)
- Sound Effects
- Disable AirDrop Ping
- Disable Charge Sound
- Disable Low Battery Sound
- Disable Payment Sounds
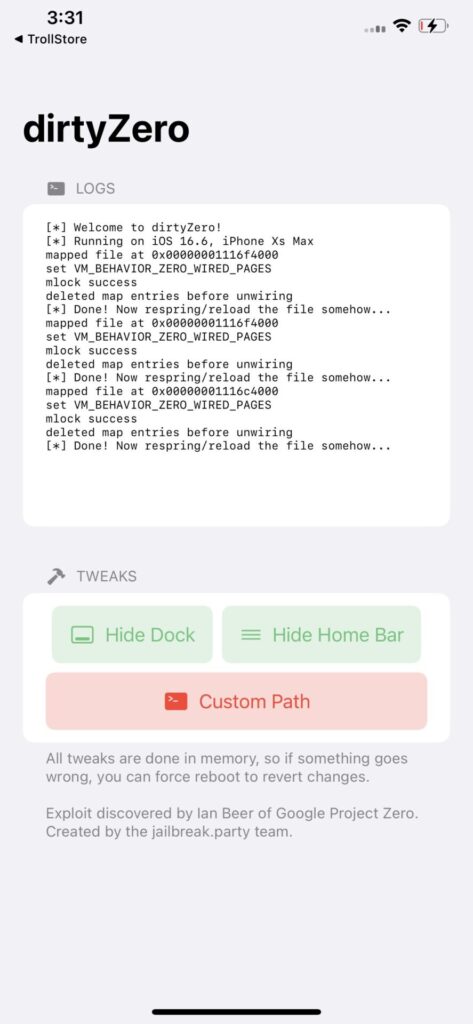
Under the buttons, you can find a text console that displays the exploit status for debugging purposes. It also displays the device info, such as the model and current iOS version.
From my testing, the exploit is reliable enough. The app works well, however, a significant drawback is that you have to manually respring the device after you apply tweaks for them to take effect. I detail the methods for manual respring below.
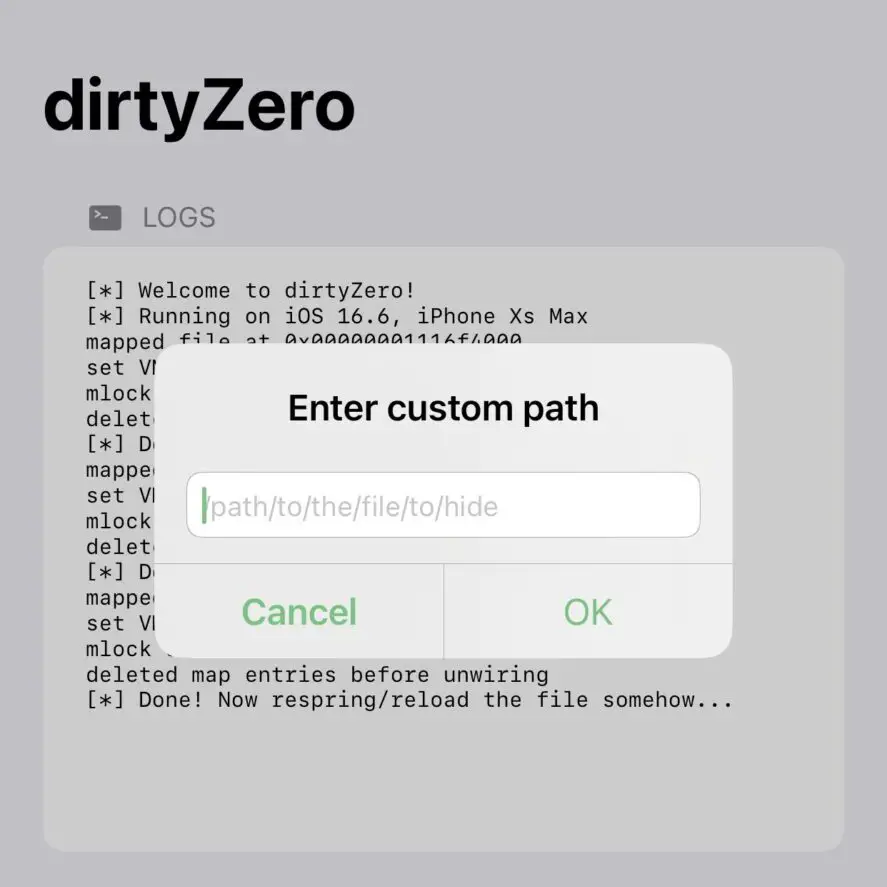
How to manually respring iOS to apply the tweaks?
Due to the limitations of the exploit used, you need to manually respring the device for tweaks to take effect. There are two ways of doing that:
- Change the device language back and forth (this makes the device respring).
- Change the Display Zoom setting in Settings -> Display & Brightness.
For the second option, just switch between the two options: Standard vs Bigger Text. You can revert to your preferred one immediately.
How dirtyZero Uses the CVE-2025-24203 Exploit to Customize iOS
This customization tool for iOS is based on the recently released CVE-2025-24203 vulnerability discovered by Ian Beer of Google Project Zero, which was presumably patched in iOS 18.4.
The CVE-2025-24203 vulnerability exploits a bug in Apple’s XNU kernel virtual memory (VM) subsystem, particularly the VM_BEHAVIOR_ZERO_WIRED_PAGES flag, which can be set by any process on its own vm_map_entry.
Once set, and under the right conditions, it causes physical memory pages to be zeroed, even if the process shouldn’t be allowed to modify those pages (e.g., they back a read-only, root-owned file).
- The app opens a root-owned, read-only file and uses
mmap()to map a page. - It marks the
vm_entryfor that page withVM_BEHAVIOR_ZERO_WIRED_PAGES. - The page is wired into memory using
mlock()(unprivileged). - The page is then deallocated using
mach_vm_deallocate(), triggering cleanup.
During the cleanup phase of the exploit:
- The page is looked up with
VM_PROT_NONE, bypassing write checks. - If the
zero_wired_pagesflag is set, the page is zeroed viapmap_zero_page().
The physical memory backing the file is now zeroed without write permissions, and you can modify protected files. It’s quite a clever exploit.
Version v1.1 was released on August 23rd, 2025 with the following changes:
- Redesigned UI (by @lunginspector)
- New tweaks and compatibility improvements for iOS 16 & 17 (by @lunginspector)
- Built-in version checker & compatibility notices
- Improved tweak applying backend and logging
- Developers can now use updated exploit code to zero out a specific offset of a file page
Frequently Asked Questions
What is dirtyZero IPA?
dirtyZero IPA is a free, open-source iOS customization app that allows users to hide the dock and home bar on iOS 16.0 – 18.3.2 without jailbreaking their device.
Is dirtyZero IPA safe to use?
Yes, the IPA is safe to use. It’s open-source and developed by Skadz using a public iOS exploit discovered by Ian Beer of Google Project Zero. You can also compile the app yourself for full transparency.
Does dirtyZero IPA require a jailbreak?
No. The IPA works without a jailbreak. It uses a userland exploit to apply visual tweaks like hiding the dock and home bar without modifying system files.
What iOS versions are supported by dirtyZero IPA?
The tweak supports iOS versions 16.0 through 18.3.2. iOS 18.4 and newer are not supported due to the exploit being patched by Apple.
How do I install dirtyZero IPA on my iPhone?
You can sideload the IPA using tools like AltStore, Sideloadly, Feather, or ESign. Once installed, open the app from your Home Screen and apply the desired customization.
Can I revert the changes made by dirtyZero?
Yes. Simply disable the toggles in the app and respring your device to restore the default dock and home bar appearance.
More iDevice Central Guides
- iOS 17 Jailbreak RELEASED! How to Jailbreak iOS 17 with PaleRa1n
- How to Jailbreak iOS 18.0 – iOS 18.2.1 / iOS 18.3 With Tweaks
- Download iRemovalRa1n Jailbreak (CheckRa1n for Windows)
- Dopamine Jailbreak (Fugu15 Max) Release Is Coming Soon for iOS 15.0 – 15.4.1 A12+
- Cowabunga Lite For iOS 16.2 – 16.4 Released in Beta! Install Tweaks and Themes Without Jailbreak
- Fugu15 Max Jailbreak: All Confirmed Working Rootless Tweaks List
- iOS 14.0 – 16.1.2 – All MacDirtyCow Tools IPAs
- iOS Jailbreak Tools for All iOS Versions