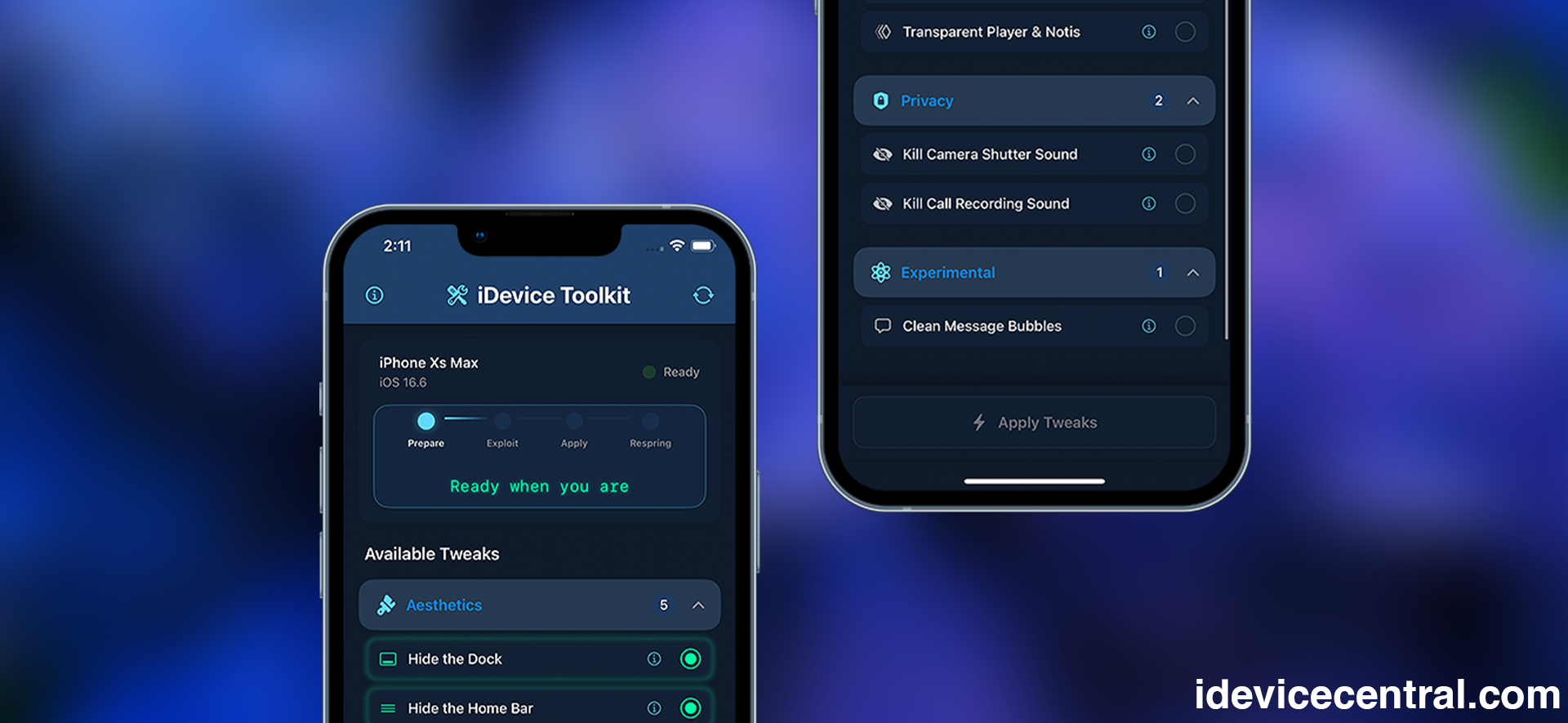
I’ve released a brand-new iOS customization tool called iDevice ToolKit, designed specifically to enable jailbreak-like tweaks on iOS 16.0 – 18.5—without needing a jailbreak. Developed here at iDevice Central, it uses the latest CVE-2025-24203 exploit by Ian Beer to modify in-memory files safely.
iDevice ToolKit lets you enable jailbreak-like tweaks and customizations on iOS 16.0 all the way up to iOS 18.3.2 on all devices. While this is not a jailbreak, it allows some customization on iOS that I believe you will find neat.
What is iDevice ToolKit?
The iDevice ToolKit application is a project I built especially for iDevice Central, and it takes advantage of the CVE-2025-24203 exploit to modify files in memory. This allows us to enable some jailbreak-like tweaks even on iOS 18.
The vulnerability is not a powerful one, but it’s enough to be able to zero out files in RAM, and a lot can be done with just that.
Here’s the full iOS compatibility chart:
iOS Version | Support Status |
|---|---|
iOS 16.0 – iOS 16.7.10 | Supported |
iOS 17.0 – iOS 17.7.5 | Supported |
iOS 17.7.6+ | Partial support (File Manager, IPA Tweak Injector) |
iOS 18.0 – iOS 18.3.2 | Supported |
iOS 18.4+, iOS 26 Beta | Partial support (File Manager, IPA Tweak Injector) |
This app is similar to mdc0 by Huy Nguyen, mdc0 UI by straight_tamago and timi2506, and dirtyZero by Skadz, from which I derived the initial inspiration and the tweak paths (files to be zeroed out in the memory).
The app can be installed with your favorite iOS IPA Signing tool, like Sideloadly, AltStore, FlekSt0re, ESign, or even TrollStore if you have a compatible device.
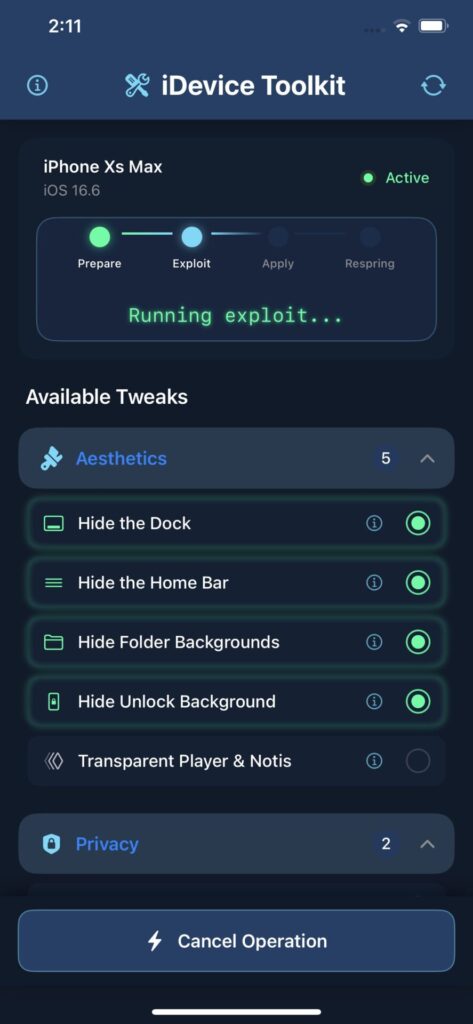
Once installed, iDevice ToolKit should be easy to use. I made the user interface modern, but I tried to keep it as easy to use as possible. I’ve also included the necessary instructions on how to perform a manual respring for tweaks to take effect.
The best part about my app is that it fetches the tweaks list directly from my GitHub repository, which means I can add new tweaks for everyone without having to necessarily provide a new IPA file.
You can even make your own custom tweaks using iDevice ToolKit by browsing system files with the built-in File Manager, and you can share the tweaks with other users. Here’s a tutorial on how to create iOS Tweaks with iDevice ToolKit.
Download iDevice ToolKit IPA
You can download the IPA file for the iDevice ToolKit customization app below. Since the app is completely free and open-source, you can also compile it yourself if you prefer.
Do keep in mind that iDevice Central (this site) and my official GitHub repo are the only official downloads for the app. I’ve also made an update checker for the app, which will tell you if a new version has been released, especially if an IPA update is necessary.
You can sideload the IPA file with your favorite iOS sideloading tools such as AltStore, Sideloadly, Feather, ESign, etc.
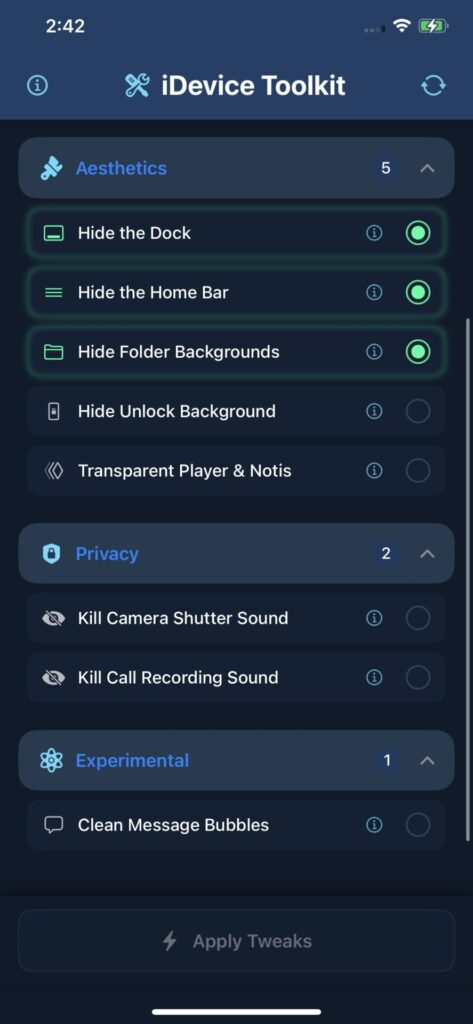
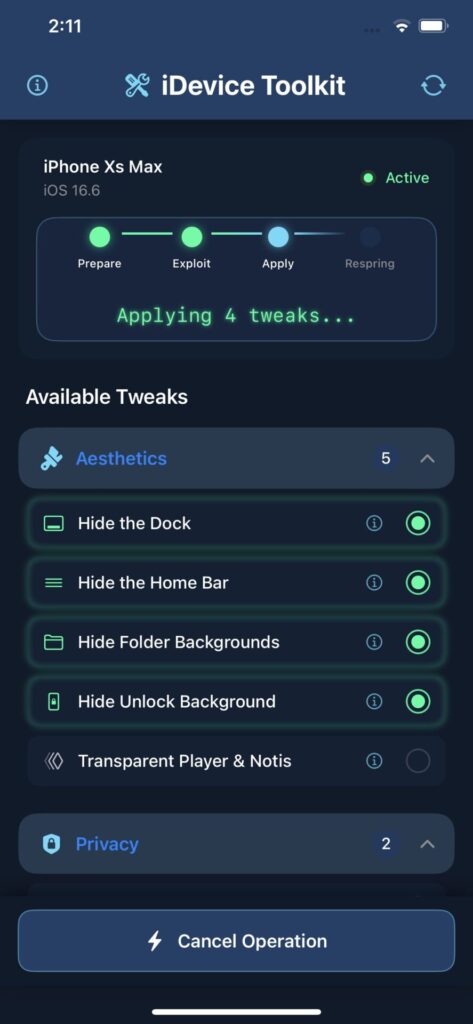
Currently Available iOS tweaks in iDevice ToolKit
Once installed, the application should be available on your Home Screen. The user interface is easy to use and has only 3 buttons:
- 🧼 Hide the Dock
- 🕹 Hide the Home Bar
- 🗂 Hide Folder Backgrounds
- 🔓 Hide Unlock Background
- 🔓 Hide Lock Icon
- 🔓 Hide Passcode Background
- 🔋 Hide Large Battery Icon
- ☀️ Disable Brightness Icon
- 🌙 Disable Do Not Disturb Icon
- 🎨 Disable App Library Background, CC Blur, Notifications, and Widgets Background.
- 📺 Transparent Media Player & Notifications
- 📷 Disable Camera Shutter Sound
- 📞 Disable Call Recording Notification Sound (iOS 18+)
- 😎 Fully Disable Emojis
- 🔊 Disable AirDrop, Low Battery, Apple Pay, and Charging audio.
- ⚙️ Make your own Tweaks directly from the app!
- 📁 File Manager to browse system files, play audio files, view images, PLISTs, etc.
- 📦 Inject jailbreak tweaks (DYLIB/Framework) into IPA files. (iOS 18.5 and lower) Use responsibly!
- More to come!
iDevice ToolKit Changelog
As I update the tool often to fix bugs or add new features, the changelog will reflect what is new and which updates are critical.
You will also be notified in the app itself when there is an important update.
v1.9.0: Preliminary iOS 26 Support + Major UI Redesign! – iOS 18.5 / iOS 26 Beta and lower (IPA)
- Preliminary iOS 26 Beta support!
- Major changes to the UI, now features a welcome screen that lets you easily pick between Cosmetic tweaks, File Manager, and IPA Tweaker!
- Bug Fixes and extra sanity checks.
v1.8.0: Added MANY new tweaks & Background Tweak Re-applying – iOS 18.5 and lower (IPA)
- Added MANY new tweaks, including audio tweaks, aesthetic tweaks etc, thanks to jailbreak.party!
- Fixed the “Disable Call Recording Notification” tweak thanks to mdc0 dev! WARNING! This tweak MAY NOT be legal in all countries. It’s YOUR responsibility to check before using! Don’t do shady things. Use responsibly and in accordance with the law!
- Added background monitoring to keep re-enabling tweaks that may require periodic re-apply. This requires location services (Always allow) and notifications to remain active in the background. No actual location data is fetched. (Trick from AltStore)
- Fixed several bugs.
v1.7.0: Fixed File Manager for Tweak Injection on IPA iOS Apps – iOS 18.5 and lower (IPA)
- A bug was fixed that caused the IPA files to not be selectable in File Picker. This is because of ESIGN / Gbox and other such signers messing up the entitlements of iDevice ToolKit when signing. Proper signing tools like Sideloadly, AltStore, etc. worked fine.
- The issue has been fixed through a workaround in iDevice ToolKit, so it should work now, but the bug in ESIGN, etc. not copying the entitlements properly remains and should be addressed by those developers.
v1.6.0: Tweak Injection for IPA iOS Apps – iOS 18.5 and lower (IPA)
- You can now inject real iOS Jailbreak tweaks (DYLIB / Framework) into IPA applications.
- Just specify the IPA file and the tweak, and the tool will combine them and give you an IPA you can either sign with AltStore / Sideloadly / ESIGN, etc., or install via TrollStore (where available).
- This module works on iOS 16.0 – iOS 18.5 on all devices. Use responsibly. iDevice Central never has and never will condone piracy!
- Fixed some UI bugs.
v1.0.5 – File Manager now available in the app! View files, folders, PLISTs, play audio, view images, etc. (IPA)
- There is now a File Manager in the app. You can access it via the folder icon in the top-right corner near the terminal. It can browse the paths available in jailed mode (/System, /Developer, etc.), it can play audio files (good for tweak development so you can disable sounds, etc.)
- The Terminal now includes a Dismiss Terminal button at the bottom to close it more easily.
- Fixed some extra bugs.
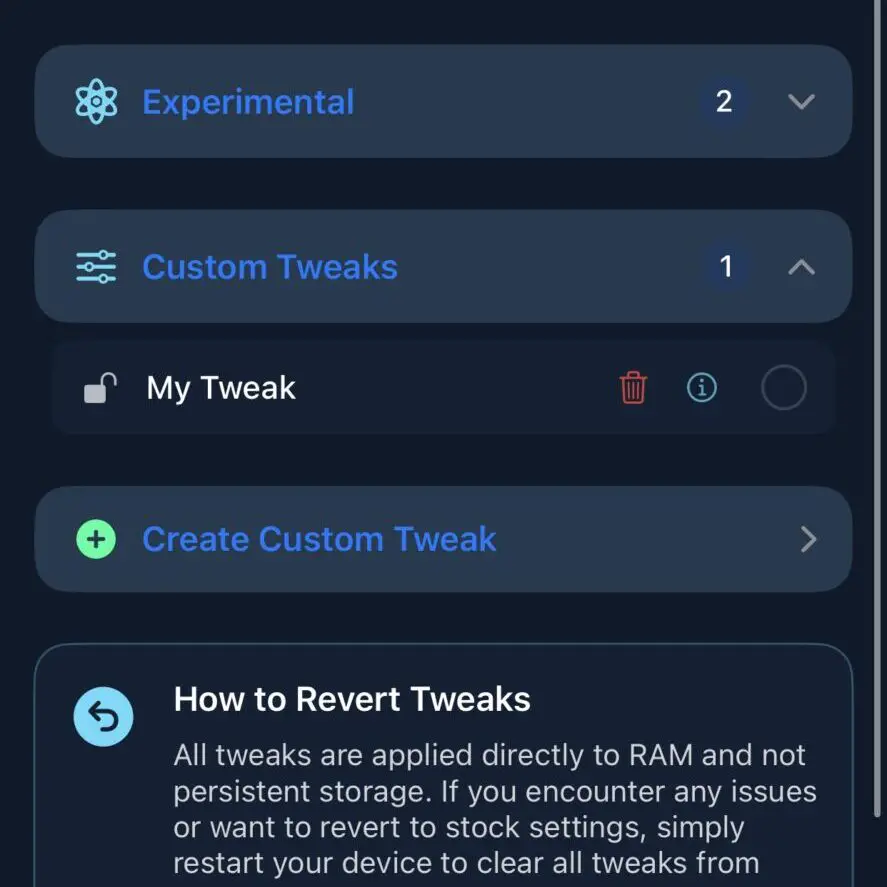
v1.0.4 – Create your own custom tweaks directly from the app! (IPA)
- You can now create your own custom tweaks and run them.
- You can share the tweaks you make.
- You can browse the file system using the built-in File Manager and select files to use in your own tweaks.
- Cleaned up the UI a bit
- Added some more tweaks
v1.0.2 – Important exploit reliability update (IPA)
- I added a terminal view (see icon at the top right corner) that keeps logs of what is going on so you can send me logs if something is not working.
- Fixed several bugs.
- Improved the exploit to no longer crash the app when a tweak fails.
- Disabled the Call Recording tweak for now. It needs work.
v1.0.1 – Important exploit reliability update (IPA)
- Switched back to the C version of the exploit, which is much more reliable. It should now work to apply tweaks with a greater success rate.
- Added info about how to revert the tweaks.
- Minor bug fixes.
v1.0 – Initial Release
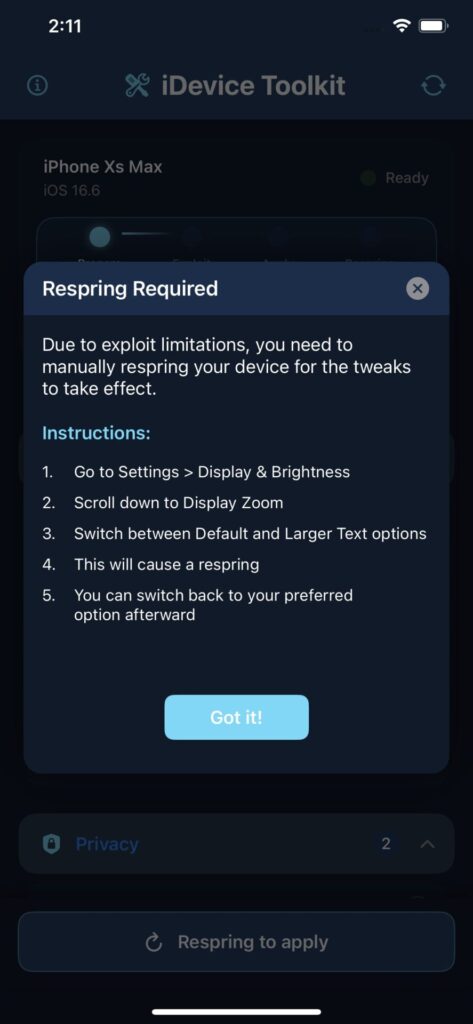
How to manually respring iOS to apply the tweaks?
Due to the limitations of the exploit used, you need to manually respring the device for tweaks to take effect. There are two ways of doing that:
- Change the device language back and forth (this makes the device respring).
- Change the Display Zoom setting in Settings -> Display & Brightness.
For the second option, just switch between the two options: Standard vs Bigger Text. You can revert to your preferred one immediately.
I’ve also provided instructions on how to manually respring inside the app.
How iDevice ToolKit Uses the CVE-2025-24203 Exploit to Customize iOS
This tweaking tool is based on the recently released CVE-2025-24203 vulnerability discovered by Ian Beer of Google Project Zero, which was presumably patched in iOS 18.4.
The CVE-2025-24203 vulnerability exploits a bug in Apple’s XNU kernel virtual memory (VM) subsystem, particularly the VM_BEHAVIOR_ZERO_WIRED_PAGES flag, which can be set by any process on its own vm_map_entry.
Once set, and under the right conditions, it causes physical memory pages to be zeroed, even if the process shouldn’t be allowed to modify those pages (e.g., they back a read-only, root-owned file).
- The app opens a root-owned, read-only file and uses
mmap()to map a page. - It marks the
vm_entryfor that page withVM_BEHAVIOR_ZERO_WIRED_PAGES. - The page is wired into memory using
mlock()(unprivileged). - The page is then deallocated using
mach_vm_deallocate(), triggering cleanup.
During the cleanup phase of the exploit:
- The page is looked up with
VM_PROT_NONE, bypassing write checks. - If the
zero_wired_pagesflag is set, the page is zeroed viapmap_zero_page().
The physical memory backing the file is now zeroed without write permissions, and you can modify protected files. It’s quite a clever exploit.

Frequently Asked Questions
What is iDevice ToolKit IPA?
iDevice ToolKit IPA is a free, open-source iOS customization app that allows users to hide the dock and home bar on iOS 16.0 – 18.3.2 without jailbreaking their device.
Is iDevice ToolKit IPA safe to use?
Yes, the IPA is safe to use. It’s open-source and developed by GeoSn0w using a public iOS exploit discovered by Ian Beer of Google Project Zero. You can also compile the app yourself for full transparency.
Does iDevice ToolKit IPA require a jailbreak?
No. The IPA works without a jailbreak. It uses a userland exploit to apply visual tweaks like hiding the dock and home bar without modifying system files.
What iOS versions are supported by iDevice ToolKit IPA?
The tweak supports iOS versions 16.0 through 18.3.2. iOS 18.4 and newer are not supported due to the exploit being patched by Apple.
How do I install iDevice ToolKit IPA on my iPhone?
You can sideload the IPA using tools like AltStore, Sideloadly, Feather, or ESign. Once installed, open the app from your Home Screen and apply the desired customization.
Can I revert the changes made by iDevice ToolKit?
Yes. Simply disable the toggles in the app and respring your device to restore the default dock and home bar appearance.
More iDevice Central Guides
- iOS 17 Jailbreak RELEASED! How to Jailbreak iOS 17 with PaleRa1n
- How to Jailbreak iOS 18.0 – iOS 18.2.1 / iOS 18.3 With Tweaks
- Download iRemovalRa1n Jailbreak (CheckRa1n for Windows)
- Dopamine Jailbreak (Fugu15 Max) Release Is Coming Soon for iOS 15.0 – 15.4.1 A12+
- Cowabunga Lite For iOS 16.2 – 16.4 Released in Beta! Install Tweaks and Themes Without Jailbreak
- Fugu15 Max Jailbreak: All Confirmed Working Rootless Tweaks List
- iOS 14.0 – 16.1.2 – All MacDirtyCow Tools IPAs
- iOS Jailbreak Tools for All iOS Versions